How does RedSpy365 Work?
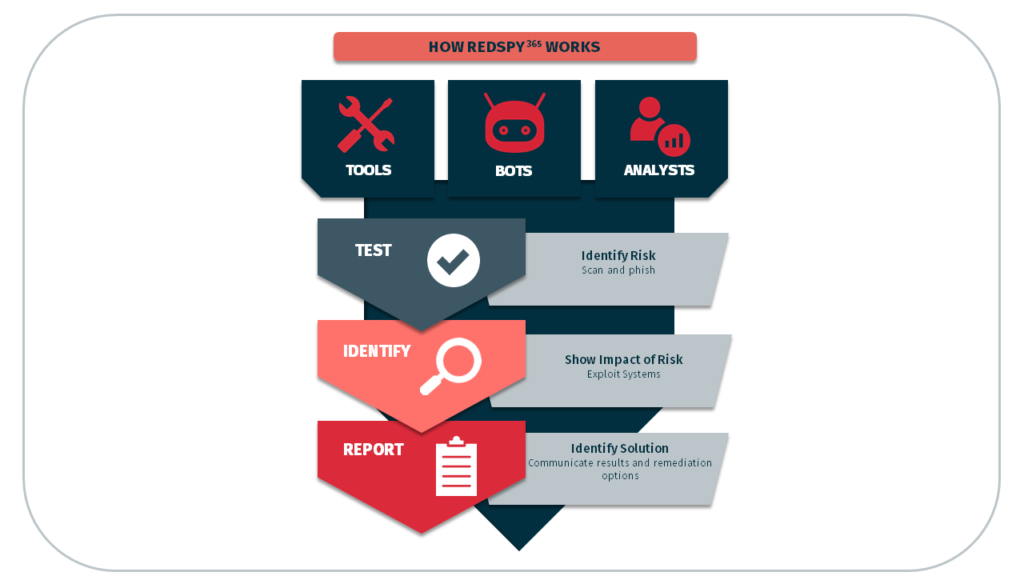
RedSpy365 is the only live, un-simulated, penetration-testing-as-a-service (PtaaS) and attack-modeling platform that is able to mimic specific hacker groups. Low-code bots help security tools to talk together and map complete attacks. Communication between bots occurs via a proprietary system of variables that are passed between security tools via the IRC channel or Slack. When keywords are noted, actions are taken—such as alerting another tool to take a subsequent action, or analyst notification.
RedSpy365 enables security tools to alert one another of important events—then eliminates false positives and duplicates, sorts by criticality, and calculates potential business impacts such as potential economic loss and interruptions to business continuity. RedSpy365 also auto-compares findings to external activity in the cybercriminal world, which further helps prioritize your limited resources.
RedSpy365 integrates with cutting-edge penetration testing and post-exploitation tools that delve much further into potential business impacts than scanning or simulated threat-modeling tools are capable of. Because of this, RedSpy365 is also able to provide much more detailed and specific troubleshooting information to correct potential cyberattack paths. The value of this troubleshooting data is enhanced because it is more likely to address root causes than similar information provided by a simulated threat-modeling or vulnerability-scanning service. Additionally, you are able to retest the threat scenario immediately after making the change to your environment, assuring you in short order that you’ve resolved the concern.
PCISS-compliant penetration tests, compliance reports, business insights reports, and executive summaries are available. Configuration is customized and can include environments such as hybrid- and multi-cloud, AWS and Azure, on-prem, devops, databases, or IoT.
RedSpy365 is available as a managed service or as a software platform that you can host and manage yourself. Contact us today for a demo and for more information.
What is the Tool Server?
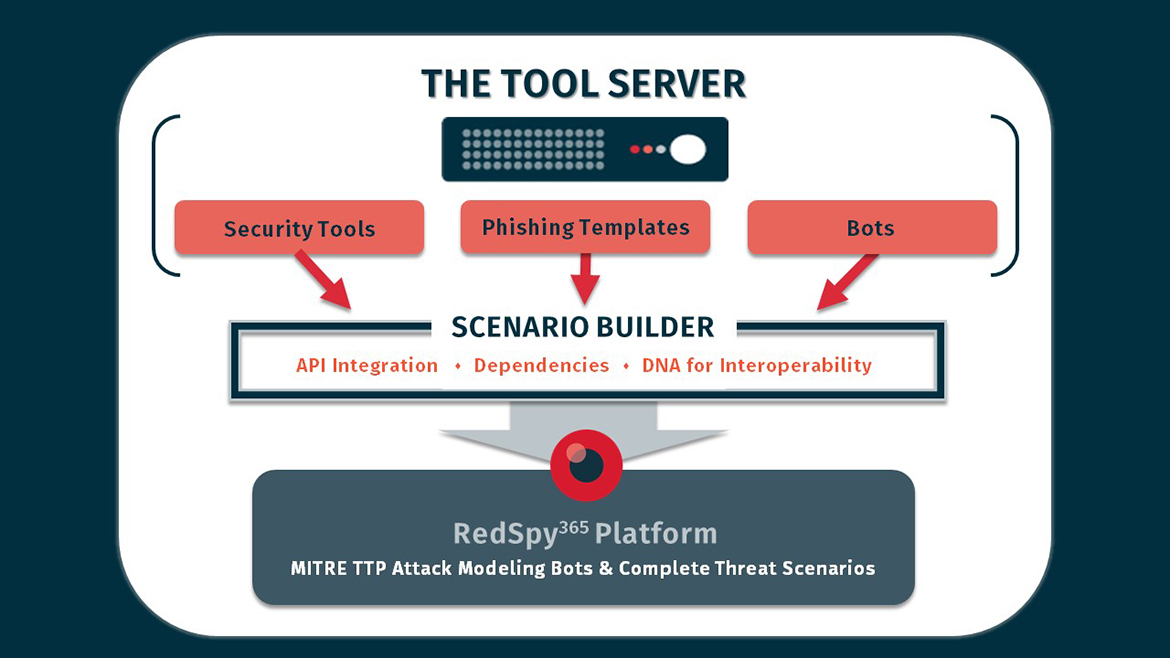
RedSpy365 leverages a combined, curated set of over 200 best-of-breed security and compliance tools; it can also integrate with your ticketing system, SIEM/SOC, or other preferred tools. Drag-and-drop security tools via the Tool Server, a central repository of security tools, phishing templates, threat scenarios, and attack bots. Share a server with RedSpy365 analysts for the latest and greatest, or host your own for a confidential, internal library.
Each tool is integrated into RedSpy365 so that it can optimally communicate with the other tools. When an element is added to the tool server, it brings with it the scripts, bots, dependencies, and other DNA to optimize impact and interoperability in the RedSpy365 environment.
| Frequently-used tools include: | ||
|---|---|---|
| Burp Suite | Icehole | Nexpose |
| Cobalt Strike | Jexboss | Nikto |
| CrackmapExec | Maltego | onesixtyone SNMP Scanner |
| dnsrecon | Masscan / Nmap | OpenVAS |
| Empire | Metasploit | Qualsys |
| Empire Powershell | MITRE Exploit Database | Slack |
| Guacamole | Nessus | SMBexec |
| Honeypots | Netsparker | Sqlmap |
Who Uses RedSpy365?

- The Management Portal is used to launch phishing tests, discover and troubleshoot the potential impacts of specific cyber threats, pull reports like 30-day summaries or full penetration tests, configure alerts, and build bots. Professional penetration testers and other IT professionals use this portal to protect, validate, and troubleshoot for their organizations or on behalf of their clients.
- The Tool Access Portal provides access to all the security tools, phishing templates, bots, and scripts that are available to be loaded into a client’s RedSpy365 environment. Threat scenarios purchased on the upcoming RedSpy365 Marketplace appear here. Within the Tool Access Portal is a Federated Dashboard that is designed for security consultancies or large enterprises to manage availability of these tools for all clients or installations at once.
- The Research Portal is designed for students, security researchers, and others to use RedSpy365 to build their own tools, threat scenarios, bots, and phishing templates for their own use or for sale on the upcoming RedSpy365 Marketplace. These tools and other elements can then be transferred from the Research Portal to the Tool Access Portal for use in a client’s environment.
- The Community Portal provides free, limited access to RedSpy365 and includes commonly-used open-source tools. Penetration testers, cybersecurity professionals, students, and others can log into this portal to learn how to use RedSpy365 and to build limited threat scenarios, bots, and scripts that can be tested against a client’s environment.
How Does RedSpy365 Manage Risk?
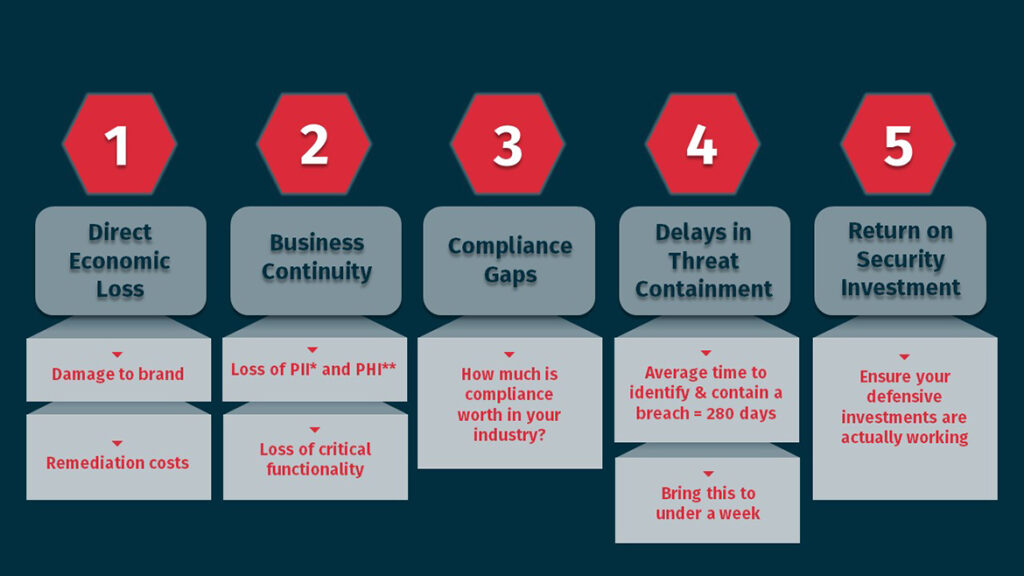
- Resilience: How quickly can your organization shut down a threat? RedSpy365 measures Mean Dwell Time (MDT), which is the total time it takes your organization to notice and contain a cyber concern. It combines many factors, such as your network configuration, the effectiveness of your defensive and detection systems, user security awareness, the actions of your IT team, and more. The resilience of your organization against attack is one important way to measure and manage cyber risk.
- Economic loss: What are the financial impacts of a potential cyberattack? Ransomware payments, corporate espionage, interruption to business continuity, exposed PII* or PHI*, and loss of business-critical documents all have their cost. Exposure to economic loss can be measured and managed by the RedSpy365 platform in a way that no other technology can. By delving deeply into the potential impacts of end-to-end attack paths—including a measure of potential economic impact called Single Loss Expectancy (SLE)—RedSpy365 is able to show real data that helps you reduce this cyber risk today.
- Critical continuity: What business processes could be disrupted? RedSpy365 creates unique value for your organization by comparing identified potential cyberattacks to the affected business processes and related essential continuity. RedSpy365 can compare findings to process ownership, and customized alerts make you aware of your remediation options, well in advance of an actual event.
- Compliance: How mature is your cybersecurity compliance? In the event of a breach, being out of compliance in carries with it a slew of risks—financial, reputational, and governance risks, to name a few. It’s tough to put a value on staying within current compliance guidelines, but RedSpy365 can help you assess and improve your complete security picture as it relates to regulatory compliance for your industry. RedSpy365 integrates with the Shared Assessments compliance tool to assess your in-scope environment for gaps in security policy, data storage, recovery planning, and more. A comprehensive compliance report provides a clear roadmap with specific suggestions.
- Return on Investment: Are your defenses actually working? When budgeting and deploying capital in the service of cyber security, there is always the risk that your efforts will fail. In the event of a breach, of course, you’d know for sure that you didn’t construct or configure your defenses correctly. RedSpy365 assures the most comprehensive, continuous support possible for testing and optimizing the investments you’ve already made—and maximize the chances of successfully fending off cybercrime. Many customers experience results similar to these in the first six months of using RedSpy365.
- A reduction in mean dwell time (MDT) from the industry average of over 200 days to less than one week
- Substantial avoidance of potential economic loss, from tens of thousands to tens of millions
- Key business continuity insights that prioritize security focus
- Increased compliance factors to nearly 100%
- A return on security investment (ROSI) of well over 300%







